[DRAFT] Web Replay Privacy & Performance
Sprig's Web Replay offering prioritizes privacy.
Privacy Overview
Every aspect of Sprig’s application, including Replays, was designed and built with user privacy as a top priority.
By default, all form content including password fields, is neither recorded nor stored. Additionally, Sprig admins can further enhance user privacy by hiding specific CSS selectors or mobile classes.
To configure Replay privacy settings, go to Settings > Heatmap & Replays > Configure.
You can disable Replays for an entire Team workspace by turning off Replays or disable them based on Product by unchecking the corresponding products under the Replays section. Disabling will mark existing Replays as paused and prevent new Replays from being launched.
Web Replay Privacy
While a replay clip may look and feel like a screen recording, Sprig's session replay clips are not actual screen recordings. They are recordings of changes in the web browser's Document Object Model (DOM), which is the data representation of the page. That record of changes is then constructed into a video that represents a user's interactions with a particular page.
This approach enables Sprig to selectively capture data, such as user interactions and form contents, while redacting other types of data, such as images and password fields.
Masking Definitions
Masking happens on device. This means any sensitive user data masked by your privacy configuration will never leave the user's device. The following definitions describe the types of masking available:
- Field masking obscures input fields with a placeholder.
- Text masking replaces characters with asterisks.
- Image masking obscures images with a placeholder.
- Interaction masking obscures interactions on the page such as clicks.
- Class masking obscures specified elements specified by ids and classes.
The minimum Web SDK version required to support the following masking definitions is Web SDK v2.22.0 or later.
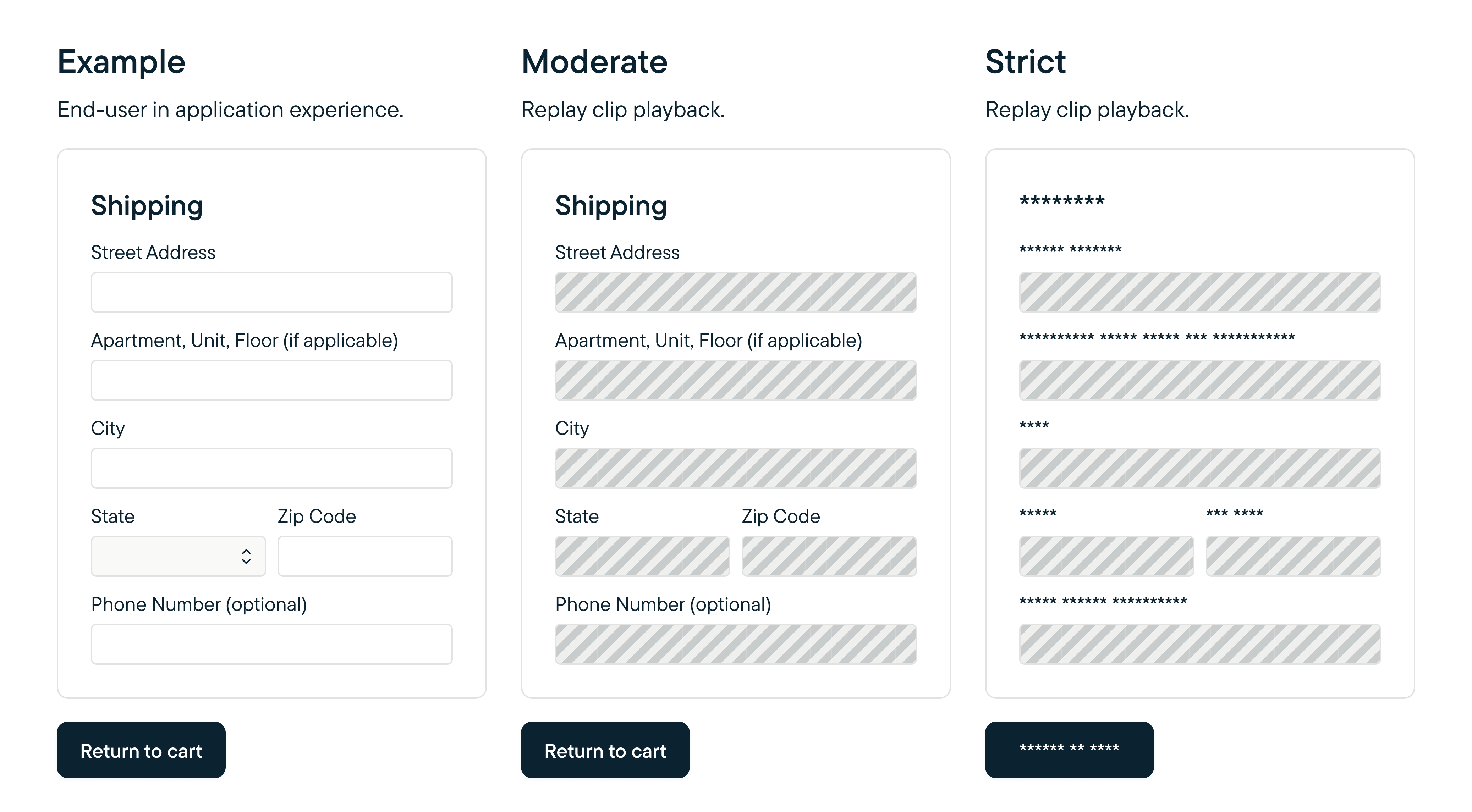
Mock up of privacy mode masking: Moderate masks only fields. Strict masks both text and fields.
Interactions
In addition to HTML content, Sprig Replays also record user interactions, such as mouse movements, clicks, screen touches, and keyboard input. Mouse movement captures are approximated during clip playback, limited to an inferred path between start and target destinations.
Compliance
In adherence to guidelines set by the California Consumer Privacy Act (CCPA), Replays does not capture nor require capturing permissions from end-users. The CCPA mandates that businesses must disclose their practices related to both the collection and sale of consumers' personal information in their privacy policies. While businesses are required to give consumers the option to opt-out of having their personal information sold to third parties, the law does not oblige them to provide a similar opt-out for just the collection of personal information.
View more information on Sprig's Privacy Policy.
We welcome feedback on our privacy practices. Please contact us at [email protected] if you have any questions or concerns.
Performance
Session Replay has been designed to use as little resources as possible. We break down performance into 4 categories: CPU, Memory, Disk and Network
CPU
We utilize the MutationObserver API to keep track of DOM changes. MutationObserver batches node changes and dispatches a joint notification which minimizes compute. These events should have very little impact on Javascript’s single-threaded performance.
Memory
Session Replay data has near zero impact on memory usage for modern web applications. Sprig immediately moves any data to IndexedDB to keep memory usage low and to persist replay across page loads.
Disk
As mentioned in the section above, Sprig uses IndexedDB to store and retrieve Session Replay data. Sprig throttles its use of IndexedDB to not exceed 2 writes per second. Sprig regularly deletes old replay data to minimize disk usage and preserve privacy.
Network
Sprig uploads Session Replay data in one request as opposed to other solutions that upload small pieces frequently. This approach improves compression efficiency, reduces network overhead and reduces energy consumption for mobile devices.
Platform | Supported | Not Supported |
|---|---|---|
Web | Class masking, password field masking, | Interactions masking. |
iOS | Masks form content and sensitive text. | Masking by class, interactions masking, image masking. |
Android | Class masking, password field masking, | Interactions masking. |
Legacy Masking Mapping - Implementation Use
iOS SDK v4.23.9 or earlier
| Platform | Basic | Moderate | Strict |
|---|---|---|---|
| Web | Hides password fields only. | Hides all text fields only. | Hides all text and images. |
| iOS | Hides text fields with UITextFields or UITextViews. | Hides text fields with UITextFields or UITextViews. | Hides all text. |
| Android | Hides text fields with TYPE_NUMBER_VARIATION_PASSWORD. | Hides EditText and TextView. | Hides EditText, TextView, ImageView and MapView. |
Privacy Controls (KURT EDIT HERE)
Privacy settings can be configured at Settings > Replays > User privacy.
iOS
Latest — iOS SDK v4.23.10 or later
-
Basic:
- No masking.
- Interactions will be captured.
-
Moderate (Default):
- UITextView, UIPickerView and UITextField and subclasses of these types will be masked`.
- Interactions will be captured.
-
Strict:
Same masking as in Moderate plus:
- UILabel, UISegmentedControl and subclasses of theses classes, as well as RCTTextView (for React Native) will be masked.
- UIImageView and subclasses of this type will be masked.
- Interactions will not be captured.
In addition to the above:
- Classes that conform to UITextInputTraits with the isSecureTextEntry property set to true will always be masked.
- Mask classes in the Advanced Privacy section will be masked.
- Unmask classes in the Advanced Privacy section will not be masked.
Legacy — iOS SDK v4.23.9 or earlier
- Basic (Default): Masks text in UITextView, UIPickerView and UITextField or subclasses of these classes.
- Full: Same as Basic privacy plus masking of UILabel and UISegmentedControl or subclasses of these classes, and RCTTextView (for React Native).
Android
By default, all secure form content on Android, including password fields, are not recorded or stored by default. Input fields configured with the TYPE_NUMBER_VARIATION_PASSWORD attribute are automatically masked, ensuring that sensitive numeric input is obscured to enhance privacy and security.
Updated about 2 months ago
